- Python Code For Aes Key Generation Download
- Python Code For Aes Key Generation Free
- Aes Python Code
- Python Code For Aes Key Generation 2
- Python Program For Aes Key Generation
This is an exercise in secure symmetric-key encryption, implemented in purePython (only built-in libraries used), expanded from Bo Zhu's (http://about.bozhu.me)AES-128 implementation at https://github.com/bozhu/AES-Python
- AES-128, AES-192 and AES-256 implementations in pure python (very slow, butworks).Results have been tested against the NIST standard (http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf)
- CBC mode for AES with PKCS#7 padding (now also PCBC, CFB, OFB and CTR thanks to @righthandabacus!)
encryptanddecryptfunctions for protecting arbitrary data with apassword
I take it you want a random key that you can use - not quite sure what the purpose of in order to make decryption not possible? – Jon Clements Mar 29 '15 at 10:35 Only one time pad can make decryption impossible without knowing the key, but good cryptography algorithms can make decryption very difficult. – user4098326 Mar 29 '15 at 10:46.
Note: this implementation is not resistant to side channel attacks.
An access key grants programmatic access to your resources. This means that the access key should be guarded as carefully as the AWS account root user sign-in credentials. It's a best practice to do the following: Create an IAM user and then define that user's permissions as narrowly as possible. Create the access key under that IAM user. Aws access key id. Sign in to the AWS Management Console and open the IAM console at. In the navigation pane, choose Users. If necessary, add the Access key ID column to the users table by completing the following steps. The Access key ID column shows each access key ID. To create access keys for your AWS account root user, you must use the AWS Management Console. A newly created access key has the status of active, which means that you can use the access key for CLI and API calls.
Python Code For Aes Key Generation Download
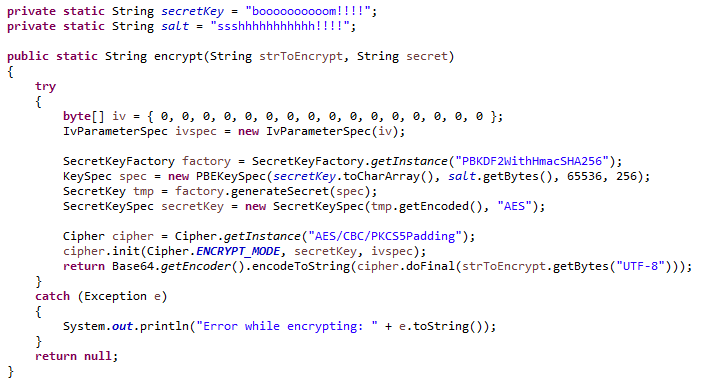
Although this is an exercise, the encrypt and decrypt functions shouldprovide reasonable security to encrypted messages. It ensures the data iskept secret (using AES), blocks are encrypted together (CBC), the samemessage encrypted twice will have different ciphertexts (salt), the ciphertexthasn't been tampered with (HMAC) and the key has some defense against brute-force(PBKDF2).
The algorithm is as follows:
Python Code For Aes Key Generation Free
-
16 random bytes of salt are extracted from the system's secure random numbergenerator (usually /dev/urandom)>
-
The given master key is stretched and expanded by PKBDF2-HMAC(SHA256) usingthe salt from 1), to generate the AES key, HMAC key and IV (initializationvector for CBC).
-
The given message is encrypted with AES-128 using the AES key and IV fromstep 2), in CBC mode and PKCS#7 padding.
-
A HMAC-SHA256 is generated from the concatenation of the salt from 1) andthe ciphertext from 3).
-
The final ciphertext is HMAC + salt + ciphertext.
Aes Python Code
Security overview:
Python Code For Aes Key Generation 2
- Fernet (symmetric encryption)¶ Fernet guarantees that a message encrypted using it cannot be manipulated or read without the key. Fernet is an implementation of symmetric (also known as “secret key”) authenticated cryptography. Fernet also has support for implementing key rotation via MultiFernet. Class cryptography.fernet.Fernet (key) source ¶.
- Sep 08, 2014 The given message is encrypted with AES-128 using the AES key and IV from step 2), in CBC mode and PKCS#7 padding. A HMAC-SHA256 is generated from the concatenation of the salt from 1) and the ciphertext from 3). The final ciphertext is HMAC + salt + ciphertext.
Python Program For Aes Key Generation
-
The random salt ensures the same message will map to different ciphertexts.
-
The HMAC ensures the integrity of both the entire ciphertext and the PKBDF2salt; encrypt-then-mac prevents attacks like Padding Oracle.
-
Bytes from keys, iv and salt are not reused in different algorithms.
-
PBKDF2 key stretching allows for relatively weak passwords to be used as AESkeys and be moderately resistant to brute-force, but sacrificing performance.